Please, share ❤️
After invading Ukraine on land and bombing our homes from the air, Russian forces have also started hacking state digital systems and spreading disinformation.
That’s what motivated our Technological R&D Lead — Sergii Kryvoblotskyi — to develop a tool that analyses where the apps you’re using take your data. At first, the idea was to help Ukrainians protect their online data from Russian law enforcement agencies, but then we’ve decided that all macOS users worldwide could use it.
Where did it all begin
When Russia started a full-scale war against Ukraine, MacPaw was prepared and focused on providing for our employees’ physical and digital safety — taking the provision of humanitarian aid through our Fund as the next step.
However, we were not alone in our efforts. All macpawians in safety began applying their knowledge and resources to help resist the war by volunteering, joining the Armed Forces of Ukraine, and spreading truthful information about the war.
Our Tech R&D Lead — Sergii Kryvoblotskyi — has extensive experience in data protection. When he saw Ukrainian digital infrastructure suffering numerous cyberattacks, he decided to take action:
“As a Tech R&D team before the war, we did a lot of research. So I began to check which of them could contribute to the country’s informational security. One of these researches was about the technical implementation of network filtering on macOS. I’ve realized it could be well-applied to protecting computers from potentially dangerous apps and adapted to help users in our new reality.”
Why protecting your data is crucial in these unstable times
You may not know it, but in July 2016, Russia enforced Federal bills No. 374-FZ and 375-FZ, which require telecom providers to store the content of voice calls, data, images, and text messages on Russian servers for 6 months, and their metadata (e.g., time, location, message sender, and recipients) for 3 years. Online services such as messengers, emails, and social networks that use encrypted data are required to permit the Federal Security Service (FSB) to access and read their encrypted communications.
It means that all internet and telecom companies that have some presence in Russia are obliged to disclose these communications and metadata and “all other information necessary” to authorities on request without a court order. Now FSB can simply call a local office of any tech company, and bam — they have access to your photos and text history.
How SpyBuster helps with that
SpyBuster provides for users’ online security. When users install the application or surf the web, they can immediately see and block applications, services, and sites connected to Russia or Belarus.
The application also has a social significance — we can determine which sites or media connect to Russian servers and inform them about it. Many media outlets are unaware that their sites are connected to Russian servers.
And we have seen it already. While using this SpyBuster to analyze the traffic processing of one of our local Ukrainian media websites, we noticed that they have connections with Russian servers and immediately fixed the problem.
The main features of SpyBuster
The application has two tabs for now: Static Analysis and Dynamic Analysis. What do they do?
Statiс Analysis
Static Analysis shows whether the app is somehow related to Russia
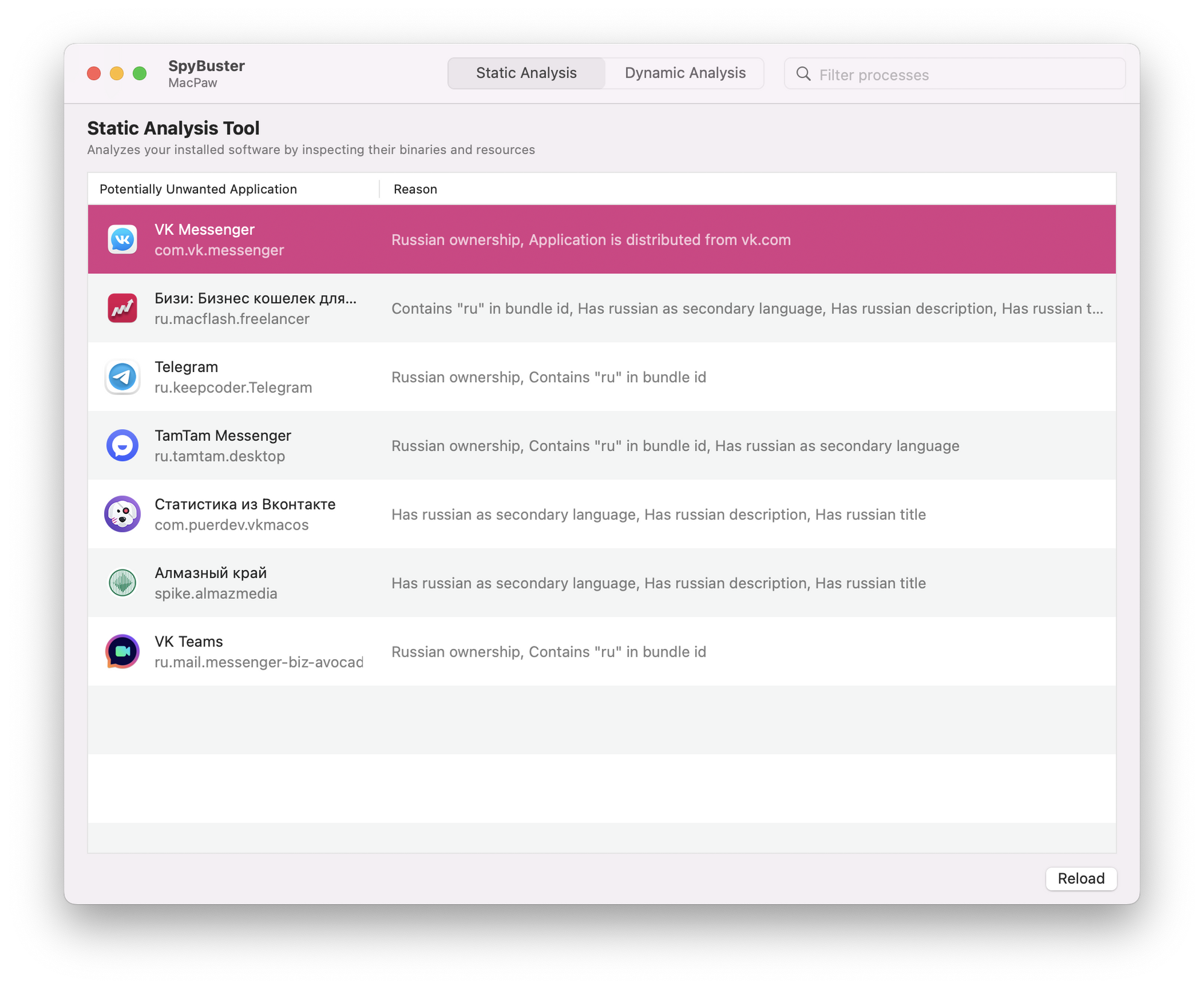 For example, it will automatically detect and highlight any apps on your Mac that are somehow related to Russia or Belarus.
For example, it will automatically detect and highlight any apps on your Mac that are somehow related to Russia or Belarus.
Dynamic Analysis
Dynamic Analysis shows how these apps and websites are behaving. When you run an app on your Mac — it starts doing something right away: sending messages to servers, writing files, gaining access, etc.
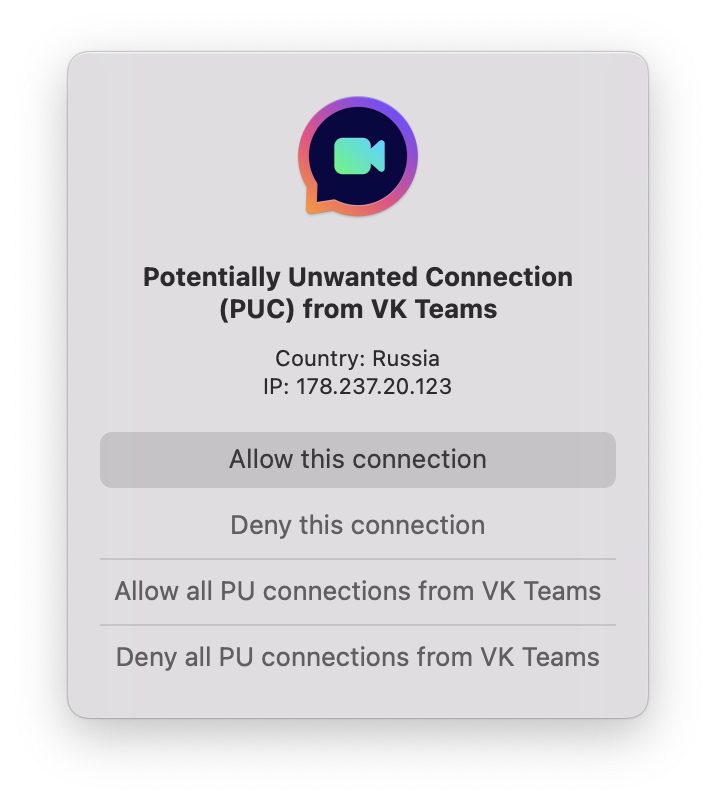
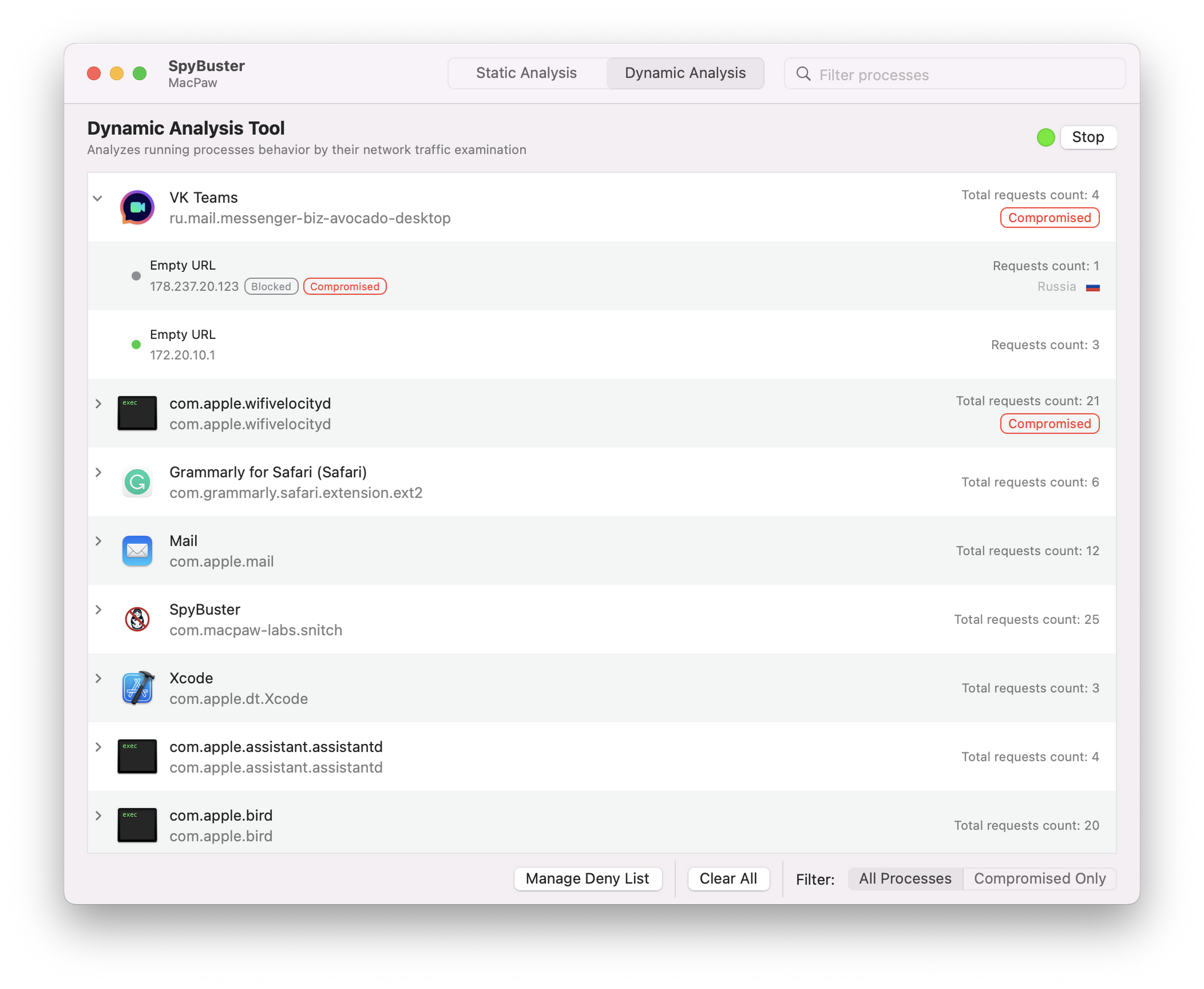 SpyBuster scans these connections in real-time and displays their history (logs) that show whether the connection was secure. You can see only the potentially threatening connections by clicking the Compromised Only button and then adding them to Deny List, so they no longer work.
SpyBuster scans these connections in real-time and displays their history (logs) that show whether the connection was secure. You can see only the potentially threatening connections by clicking the Compromised Only button and then adding them to Deny List, so they no longer work.
Please note that If you don’t disable the connection to the endpoint the app or a site is trying to reach, they will continue sending your data to insecure servers.
Tech specifications
Your Mac should run on macOS 10.15 version or higher to install the app.
How to Download
You can go to https://research.macpaw.com/spy-buster/ and download the app completely free of charge. It processes the data about the connections locally on your device only while using the app, without storing it anywhere else.
Support
If you have some more questions about the work or tech specifications of the app, please send your questions and feedback to spybuster@macpaw.com. We will try to answer as soon as possible.









Ми у соцмережах: